Protected Users group in Active Directory
Grupul Protected Users este un grup nou ce vine cu AD-ul de pe Windows 2012 R2 si care are ca scop sa zicem protejarea unor conturi sensibile din Active Directory. Nu este ceva ce as putea recomanda pentru orice scenariu pentru ca dupa cum o sa vedem poate crea si unele neplaceri pentru un admin.
By default grupul este gol, si puteti pune conturile sensibile in acest grup dupa instalarea unui DC cu Windows 2012 R2. Grupul iti ofera “protectie” in doua feluri. Odata client side si inca o data server side. Asta ce inseamna? Inseamna ca si clientul si serverul vor verifica apartenenta la acest grup si daca faci parte din el anumite decizii vor fi luate. Bineinteles, clientul trebuie sa fie aware de aceasta “optiune” (adica trebuie sa fie Windows 8.1 sau 2012 R2). Dar si un client mai vechi poate beneficia de un soi de protectie prin verificarile si actiunile facute pe partea de server.
Iata de exemplu ce se intampla daca adaug un cont de domain admin in acest grup si incerc sa accesez un server cu Windows 2012 R2 folosind adresa IP (pentru a forta folosirea protocolului NTLM in loc de Kerberos). Daca folosim Kerberos atunci accesul functioneaza perfect.
Pe scurt, NTLM-ul va fi blocat pentru membrii acestui grup. Ca si curiozitate iata si ce se vede intr-o captura de pe retea:
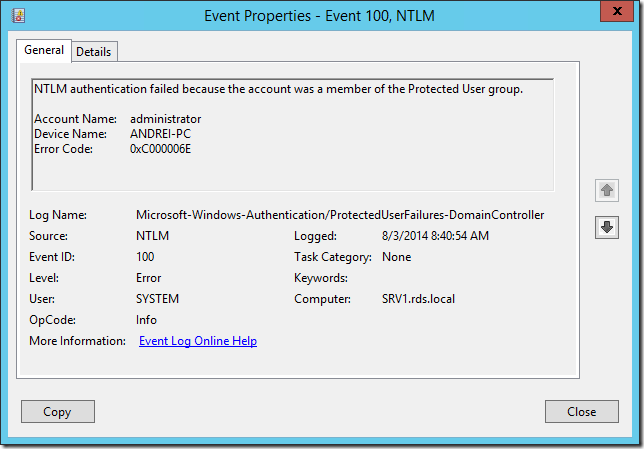
Pentru diagnostic, pe domain controller gasim si cateva loguri in categoria Aplication and Services Logs/Microsoft/Windows/Authentication si iata cam ce puteam vedea acolo:
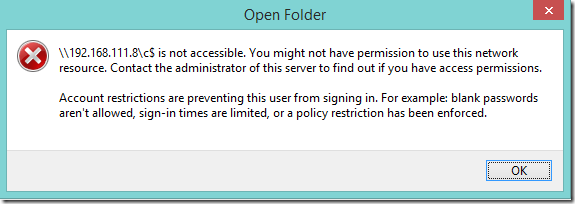
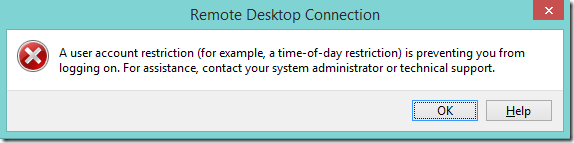
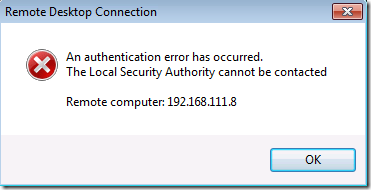
Atentie insa ca toata schema asta poate aftecta si alte servicii pe care in prima faza nu le luati in calcul. Iata ce se intampla cand incerc sa ma conectez la un domain controller folosind adresa IP (de pe un Windows 8.1):
Iar mai jos este mesajul cand incerc acelasi lucru de pe un Windows 7.
Deci mare grija cand adaugati conturile administratorilor in acest grup.
Restrictiile mai sunt valabile si atunci cand accesati un server cu o versiune de Windows mai veche, de exemplu Windows 2008, conditia fiind sa aveti toate DC-urile din domeniu cu Windows 2012 R2 (domain functional level 2012 R2).
Mai jos o sa pun restrictiile asa cum sunt listate ele pe Technet:
When Windows 8.1 devices are connecting to Windows Server 2012 R2 hosts
When the Protected Users’ group account is upgraded to the Windows Server 2012 R2 domain functional level, domain controller-based protections are automatically applied. Members of the Protected Users group who authenticate to a Windows Server 2012 R2 domain can no longer authenticate by using:
- Default credential delegation (CredSSP). Plain text credentials are not cached even when the Allow delegating default credentials Group Policy setting is enabled.
- Windows Digest. Plain text credentials are not cached even when Windows Digest is enabled.
- NTLM. The result of the NT one-way function, NTOWF, is not cached.
- Kerberos long-term keys. The keys from Kerberos initial TGT requests are typically cached so the authentication requests are not interrupted. For accounts in this group, Kerberos protocol verifies authentication at each request..
- Sign-in offline. A cached verifier is not created at sign-in.
Non-configurable settings to the TGTs expiration are established for every account in the Protected Users group. Normally, the domain controller sets the TGTs lifetime and renewal, based on the domain policies, Maximum lifetime for user ticket and Maximum lifetime for user ticket renewal. For the Protected Users group, 600 minutes is set for these domain policies.
After the user account is added to the Protected Users group, protection is already in place when the user signs in to the domain.
When domain controllers other than Windows Server 2012 R2 require the Protected Users security group
The Protected Users group can be applied to domain controllers that run an operating system earlier than Windows Server 2012 R2. This allows the added security that is achieved by using the Protected Users group to be applied to all domain controllers. The Protected Users group can be created by transferring the primary domain controller (PDC) emulator role to a domain controller that runs Windows Server 2012 R2. After that group object is replicated to other domain controllers, the PDC emulator role can be hosted on a domain controller that runs an earlier version of Windows Server.
For more information, see How to Configure Protected Accounts.
Built in restrictions of the Protected Users security group
Accounts that are members of the Protected Users group that authenticate to a Windows Server 2012 R2 domain are unable to:
- Authenticate with NTLM authentication.
- Use DES or RC4 encryption types in Kerberos pre-authentication.
- Be delegated with unconstrained or constrained delegation.
- Renew the Kerberos TGTs beyond the initial four-hour lifetime.
Ar mai fi multe de spus despre Protected Groups insa documentatia este inca foarte subtire pe acest topic si cred ca va fi folosit in foarte putine cazuri. De tinut minte ca poate cauza multe probleme cand nu a fost testat cum trebuie inainte de implementare si avut grija atunci cand inca mai aveti DC-uri cu Windows 2003 (e posibil sa blocheze si autentificarea Kerberos).
De ajutor in a intelege cum functioneaza mai este si pagina de aici: http://technet.microsoft.com/en-us/library/dn518179.aspx