Azure AD Connect – Single Sign On (SSO)
Am scris prin Ianuarie despre noi functionalitati in AD Connect. Si mai exact am scris despre Azure AD Pass Through Authentication. Dar mai este ceva nou in AD Connect. Si anume optiunea de SSO in cloud ce poate functiona chiar si impreuna cu Pass-through Authentication, fara a mai fi nevoie de ADFS sau alte componente; doar AD Connect.
Ca si mentiune, aceasta optiune de SSO functioneaza pentru clientii ce sunt joinati in domeniul AD on premises si pot contacta un domain controller (poate fi chiar si via VPN).
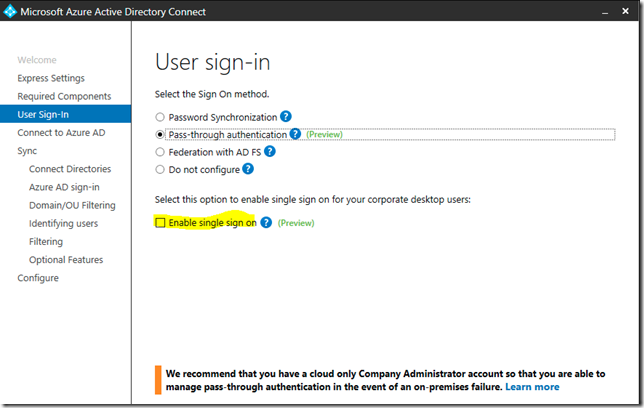
Iata cerintele aici:
SSO is a feature that is enabled through Azure AD Connect and works with password sync or Pass-through authentication and your on-premises Active Directory. For your end users to use single sign-on in your environment, you need to ensure that users are:+
- On a domain joined machine
- Have a direct connection to a domain controller, for example on the corporate wired or wireless network or via a remote access connection, such as a VPN connection.
- Define the Kerberos end-points in the cloud as part of the browser’s Intranet zone.
If any of these requirements are not present, such as the machine is off the corporate network, then the user is prompted to enter their password as they would without single sign-on.
Nota: Trebuie sa mentionez ca SSO din Edge nu merge deocamdata. Poate pe viitor. In schimb mie mi-a functionat din Chrome si IE.
Imaginea din documentatia de aici cu modul de autentificare arata cam asa:
In principiu este Integrated Windows Authentication (IWA) si Kerberos, folosind si acel computer account creat de AD Connect (AZUREADSSOACCT).
Clientul va discuta cu DC-ul local, ce va incripta un ticket cu informatiile din computer accountul AZUREADSSOACCT ce va fi mai apoi decriptat in Azure.
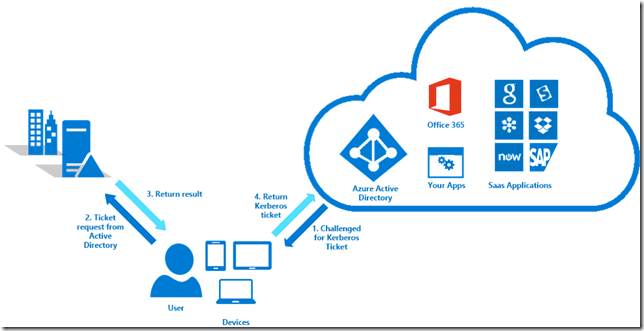
Iata si toti pasii pe care ii parcurge clientul:
- Azure AD challenges the client, via a 401 Unauthorized response, to provide a Kerberos ticket.
- The client requests a ticket from Active Directory for Azure AD.
- Active Directory locates the machine account, created by Azure AD Connect, and returns a Kerberos ticket to the client encrypted with the machine account’s secret. The ticket includes the identity of the user currently signed in to the computer.
- The client sends the Kerberos ticket it acquired from Active Directory to Azure AD.
- Azure AD decrypts the Kerberos ticket using the previously shared key. Then it either returns a token to the user or asks the user to provide additional proofs such as multi-factor authentication as required by the resource.
Cerintele sunt putin diferite pe partea de networking daca folositi Password Sync. Daca folositi Pass-through, nu mai este nevoie de nimic suplimentar.
If you are enabling ‘Single Sign On’ with ‘Password Sync’, and if there is a firewall between Azure AD Connect and Azure AD, make sure that:
- The Azure AD Connect server can communicate with *.msappproxy.net
- Azure AD Connect can make HTTPS requests to Azure AD on the ports below:
Protocol
Port Number
DescriptionHTTPS
9090
Enable SSO registration (required only for the SSO registration process).
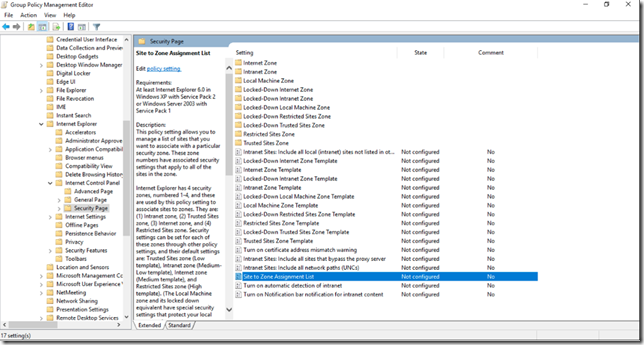
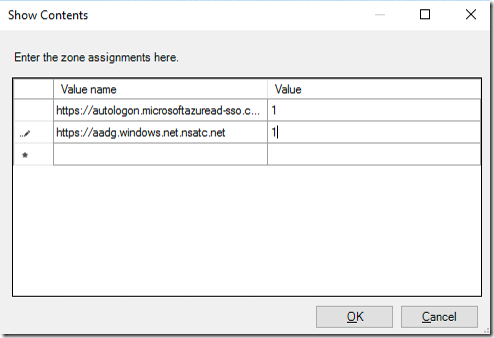
In afara de asta mai e nevoie de inca o configurare pe statii (ce se poate face prin GPO) ce va permite browserului sa trimita ticketul Kerberos catre Azure (si anume sa fie adaugate in intranet zone). Site-urile necesare sunt:
https://autologon.microsoftazuread-sso.com
https://aadg.windows.net.nsatc.net
Puteti folosi Site to Zone Assignment List aflat in User Configuration\Administrative Templates\Windows Components\Internet Explorer\Internet Control Panel\Security Page:
Gasiti toate detaliile necesare in documentatia oficiala:
https://docs.microsoft.com/en-us/azure/active-directory/connect/active-directory-aadconnect-sso
Si tineti minte, nu merge cu Edge deocamdata.